728x90
Code review
다음 코드를 보고 alg: none을 이용한 공격을 생각해보자. 다음 토큰을 사용한다.
eyJhbGciOiJub25lIiwidHlwIjoiSldUIn0.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG
9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.try {
Jwt jwt = Jwts.parser().setSigningKey(JWT_PASSWORD).parseClaimsJws(accessToken);
Claims claims = (Claims) jwt.getBody();
String user = (String) claims.get("user");
boolean isAdmin = Boolean.valueOf((String) claims.get("admin"));
if (isAdmin) {
removeAllUsers();
} else {
log.error("You are not an admin user");
}
} catch (JwtException e) {
throw new InvalidTokenException(e);
try {
Jwt jwt = Jwts.parser().setSigningKey(JWT_PASSWORD).parse(accessToken);
Claims claims = (Claims) jwt.getBody();
String user = (String) claims.get("user");
boolean isAdmin = Boolean.valueOf((String) claims.get("admin"));
if (isAdmin) {
removeAllUsers();
} else {
log.error("You are not an admin user");
}
} catch (JwtException e) {
throw new InvalidTokenException(e);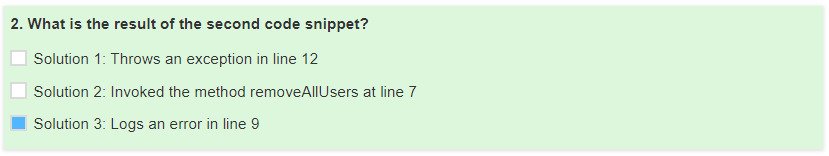
728x90
'강의 및 교육 > Inflearn - Webgoat' 카테고리의 다른 글
| JWT tokens - 10. Refreshing a token (0) | 2022.02.14 |
|---|---|
| JWT tokens - 8. JWT cracking (0) | 2022.02.11 |
| JWT tokens - 5. JWT signing (0) | 2022.02.10 |
| JWT tokens - 3. Decoding a JWT token (0) | 2022.02.10 |
| Authentication Bypasses - 2. 2FA Password Reset (0) | 2022.02.09 |


